DKIM records
DKIM (DomainKeys Identified Mail) is an email security standard designed to make sure messages aren’t altered in transit between the sending and recipient servers. If a DKIM record is added to a domain, it increases the deliverability of emails.Sending mail directly
If your application sends mail directly, you can simply add a DKIM record to your configuration object as a TXT record (see Installation), e.g.:Text
Sending mail through a 3rd party
If your application sends email using a 3rd party service configured by your customer (e.g. Google Workspace, Zoho Mail, or Microsoft 365), your Entri account manager can enable a DKIM prompt that walks your customers through setting up DKIM using those services. Once DKIM is enabled for your application, the Entri modal will detect what email provider a domain uses (Entri supports Google Workspace, Microsoft 365, Zoho Mail). Depending on the provider, Entri will show instructions for how to set up DKIM after the other types of records have been added. If Entri detects that DKIM has already been set up, we will skip this step. For example: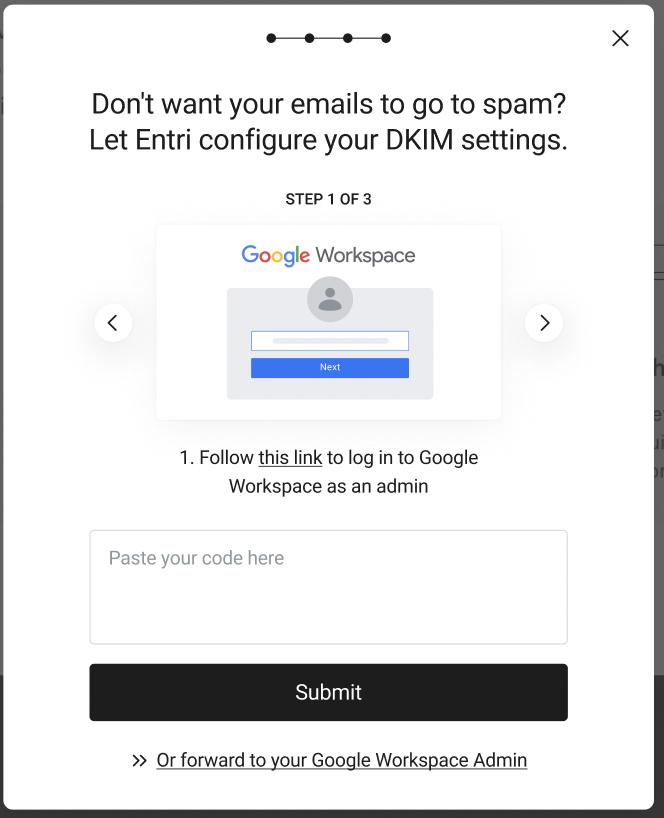
SPF records
Important When providing Entri the SPF record using the script found on
the Installing Entri page, the record type must be identified as
TXT.
Text
Text
Text
Text
ImportantIf Entri compares the existing record with the record from the end-user and there’s a conflict with the appendix (~all vs -all) then we will use ~all by default. ~all is recommended as it minimizes SPF errors.
How GoDaddy Uses Nested Includes for SPF
When handling SPF records through Domain Connect, GoDaddy follows a strategy that avoids directly modifying the root domain’s existing SPF record. Instead, GoDaddy creates a dedicated subdomain (typically in the form ofdc-<random_string>._spfm.<domain>) and publishes its SPF configuration there. This subdomain contains the necessary mechanisms, such as ip4, ip6, or additional include statements, to authorize GoDaddy’s sending infrastructure. The main SPF record on the root domain is then updated to reference this subdomain using an include mechanism (e.g., include:dc-<random_string>._spfm.<domain>). This approach creates a nested include, where the parent SPF record delegates authorization to GoDaddy via the subdomain. This method helps keep the root SPF record cleaner, allows modular updates to the provider-specific SPF content, and reduces the risk of accidentally breaking existing SPF configurations.
For example, consider a domain mydomain.com that initially has the following SPF record:
Text
Text
Text
GoDaddy SPF Records and Webhooks
Our propagation check process is designed to account for nested SPF structures, such as those used by GoDaddy through Domain Connect. When verifying record propagation, Entri Connect will follow include chains and subdomain delegations to ensure that the original SPF record specified in the showEntri configuration is present and resolvable under the domain. Continuing the example above, even though GoDaddy published the record as:Text
Text
DMARC records
To set up DMARC records for your users, include a TXT record with_dmarc as the host value in your configuration object (see Installation), e.g.
JavaScript
Optional: Check for existing DMARC record
If you want to check if your user has a valid DMARC record already set, and if so, not update it, you can set thevalidateDmarc property to true in your config.
Need Advanced DMARC handling? Check out our DMARC Handling: Advanced Options section!

